I’ve worked with a number of organisations this year that have been refreshing or redesigning part or all of their security function. It’s brought into focus for me the tension between new security practices and organisational inertia. These have all been organisations that cared greatly about security and were in no way dysfunctional. However, they have all been fighting the battle of five to ten years ago and were only now were undergoing the discovery and self-analysis to understand how to deliver on the aspirations they have in the new context of cyber security and the changed threat landscape.
It has brought home to me the need to focus on continual improvement activities, not limited to finding greater efficiency and effectiveness in what we are doing now but regularly challenging the scope of our activities to see if we need to do more or less or do different things.
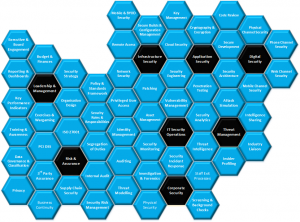
When I was at @stake, back at the turn of the century, we developed a concept of the Security Blueprint, an inelegant and semantically-confused map of the things we thought security functions should be doing. Different bits of the blueprint were more important to some sectors than others, product vendors had very different concerns to the ISPs for example. It wasn’t an enterprise security architecture, at least not compared to current sophisticated approaches to enterprise security architecture, but it was a useful tool to quickly get to the core of what an organisations security function already did, what it could do, what it needed to do and what it didn’t need to.
Having stumbled across a copy of the old @stake Security Blueprint I was struck by how much has changed since then, especially in light of the organisations I have been helping this year. I’ve created a Security Blueprint for 2013 following a similar approach, inelegant and semantically-confused but I think complete and and useful. I think I might do another one of these in 10 years time and see how much has changed since then.
Click on the image for a full size version.
This assumes a fairly standard commercial front-office/back-office IT estate with some form of direct customer interaction. It could be applied to a financial services organisation as it stands, a safety-critical organisation, an organisation with operational technology or a government department would need changes to this blueprint.