I’ve mentioned Boyd’s OODA loop in a previous post but I thought it would make sense to share how I view the OODA loop driving the development of security operations. This is in contrast to the common derivation of the Deming cycle, that is often used in security programmes: Plan, Do, Check, Act (PDCA) .
Security Operations Centres (SOC) provide an increased ability to defend our businesses and their community from determined adversaries in cyberspace. A key framing view of a SOC is to consider the relationship between the SOC and the adversaries targeting the business as a combative relationship; as such an approach typified by Robert Boyd’s OODA loop is a useful tool for thinking comprehensively about how to plan our interaction with adversaries in the cyber domain.
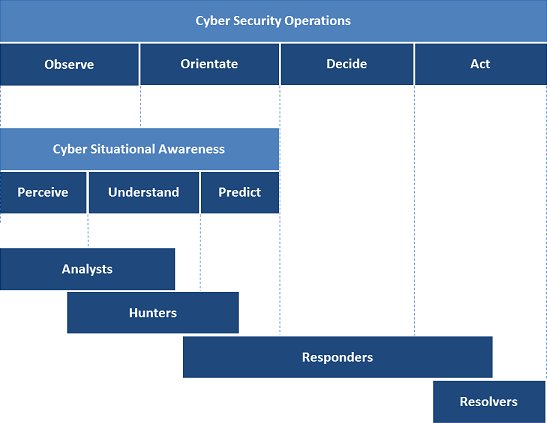
The OODA construct breaks adversarial decision making into four interrelated stages, Observe, Orient, Decide and Act. The goal of the OODA construct in adversarial situations is to be able to change the environment through action such that your adversary continually has to orient on incomplete or outdated observations and therefore makes poor and damaging decisions or falls into inaction allowing your action to succeed and ultimately for you to win the contest.
There is an inherent asymmetry between the attacker and defender in cyberspace; the attacker can try many attacks, the attacker only needs to find one exploitable weakness whereas the defender must continually defend and must defend against all possible exploitable weaknesses. However, there are advantages to being a defender, you control the environment within which the contest takes place and through preparation such as war-gaming, run books and ultimately automation you generate the ability to decide and act without extended orientation periods. There is also an opportunity for defenders to innovate and use tools and trechniques such as tar-pits, honeypots, powering down, QoS limits, disconnection, legal take downs, law enforcement disruption operations and DNS redirects to change the environment the contest is played out in to force an attacker to reorient and lose initiative.
The implication for a SOC of the OODA loop is that merely monitoring and analyzing attacks (Observe & Orient) is not enough. These activities do generate Cyber Situational Awareness but it is the Decisive Actions completed in incident response and recovery activities (Decide & Act) that complete the overall increase in cyber security from a SOC.
In developing a SOC the Cyber Security Operations team will usually grow from a reactive state of responding to problems, to a proactive state of hunting for problems before they trigger alerts; and eventually to a predictive state where likely problems are identified and managed or minimised before they occur. Much like Cyber Situational Awareness is an emergent property of the SOC these ‘states’ are the result of increasing levels of maturity across the SOC capabilities and of the ability to accelerate the progress through and the feedbacks across the SOC OODA loop.
The ultimate goal for a SOC is to provide both a high level of cyber situational awareness to detect and understand attacks as well as a fast and effective response capability to minimize the harm from attacks ultimately addressing all the components of the OODA loop.
Key Performance Indicators for SOCs should address the quality of decisions made, the effectiveness of actions taken as well as the speed of traverse the loop such as is now often typified in Mean Time to Detect (MTTD) and Mean Time to Recover (MTTR) which are starting to be used by cyber regulators to understand the effectiveness of the cyber security operations in firms they supervise.

3 thoughts on “Security Operations and the OODA Loop”
Comments are closed.