Cybersecurity has traditionally and overwhelmingly focused on resistance to cyber attack: development and deployment of cyber controls that limit the extent and mitigate the impact of attacks, with the core assumption being that the organisation will be able to prevent most attacks, and at worst, continue to function near-normally during an incident and be able to resume normal operations with minimal delay.
Robust cyber resistance frameworks such as the NIST Cyber Security Framework have emerged, but in reality, good practices that are being developed every day in the field aren’t making their way back into the standards quickly enough in order to make these frameworks practically useful in the fight against cybercrime. At the same time, we also see leading organisations that have successfully mapped out good practices, but struggle to meet their own aspirations across all affected areas of the enterprise.
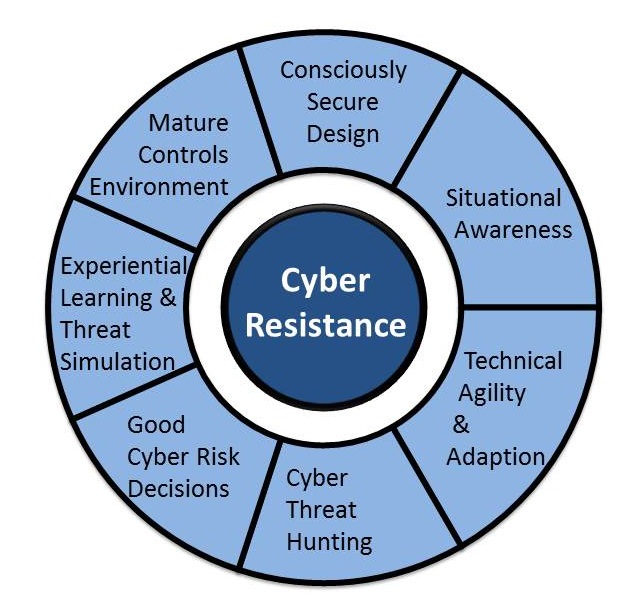
A common set of good organisational practices for cyber resistance should include the following:
|
Term |
Description | Organisational Owner |
| Situational Awareness | Understanding an organisation’s strengths, assets, critical business processes, and weaknesses, as well as likely adversary tactics, targets and capabilities. It is important that organisations continually absorb and assess new information to refresh this understanding. | CISO |
Consciously Secure Design |
Designing new product and services, and processes, and information systems that support the business with the nature of threats and their potential impact in mind. Consciously considering threat impact during design reduces the need to ‘bolt-on’ expensive, inconvenient and fragile security controls after the fact. | CISO in partnership with COO and CTO |
| Mature Controls Environment | Implementing both cyber controls and other business controls such as fraud detection, procurement, and especially IT service management. These controls guide and enforce appropriate and effective business risk decisions, including key controls that address ‘extended enterprise’ (e.g., connected supply chain) cyber risks. | CISO in partnership with CIO, CTO and CFO |
| Good Cyber Risk Decisions | Preparing staff across an organisation and the extended enterprise, from the front line to the boardroom, to make cyber risk decisions that match the organisation’s risk appetite and fully account for the threats they face. | CISO in partnership with HR |
| Cyber Threat Hunting | Utilising the core concepts and goals of incident response by proactively hunting for indicators of attacks before detective controls identify them. | CISO |
| Technical Agility and Adaption | Constantly adapting technical systems and processes in light of new threats or events. | CTO |
| Experiential Learning & Threat Simulation | Using table top cyber exercises, ‘red-teaming’, and other realistic threat simulation activities to test, teach and provide opportunities for employees, managers and board members to learn how to respond, to develop incident management ‘muscle memory’, and judge the effectiveness of an organisations’ resistance in the face of attacks from likely adversaries. | CISO in partnership with CEO or CRO |
“A financial institution’s lack of information regarding cybersecurity threats poses undue risk to itself and other financial institutions.” FFIEC Statement of Cybersecurity, November 2014
Cyber resistance is necessary, but is by no means sufficient or easy to deliver; it requires extensive, enterprise-wide focus, commitment, skills, and funding. It is becoming clear to many organisations that even the most comprehensive and expensive cybersecurity programs will fail to mitigate every threat due to constant and rapid organisational change, an aggressively competitive jobs market for cyber professionals, and a rapidly evolving threat environment.
This complete blog series can be found here:
4 thoughts on “Cyber Resilience: Part Two Resistance”
Comments are closed.