I’ve moved from the private sector back into the public sector, focusing on Health & Social Care. During my work, I am regularly reminded of the government security doctrine that was in effect when I last worked in the public sector many years ago; its influence remains even as it has now been retired and superseded. The older Information Assurance (IA) doctrine has been replaced by a combination of Information Governance (IG) and Cybersecurity. IG now has a much stronger focus on data protection, privacy and rights. Cybersecurity appears to be doing the activities that information security and IT security always did, but it has a different focus.
The older IA doctrine focused on Information Assets, which made sense when our IT systems were often ‘supportive of’ but ‘adjacent to’ business activities. However, increasingly effective cyber security concerns itself with business activities and business value generation and sustainment. Information assets are a part of this but not the whole and, in many cases, not the larger amount.
In health where I am now working, older IT systems were more for storing and retrieving information. However, as we digitise, the digital platforms are playing a significantly more central role in the actual real-world delivery of health outcomes for patients. This embedding within service delivery means that while we do worry about the security of information assets, it is the availability and integrity of the digital systems that directly drive patient outcomes that are the focus.
We focus less on Information Assets as our key point of reference and increasingly more on customer/patient outcomes (risks to morbidity and mortality impacts which derive from the operational disruption of critical care pathways) and the cybersecurity threats to those.
The financial sector (led by their regulators) made a similar shift from thinking primarily about the confidentiality of information before the 2008 crash to realising the harms from a systemic failure of service delivery and increasing the time spent focusing on the risks to the integrity and availability of ‘critical business services as part of their growing focus on systemic operational resilience following their work on systemic financial resilience.
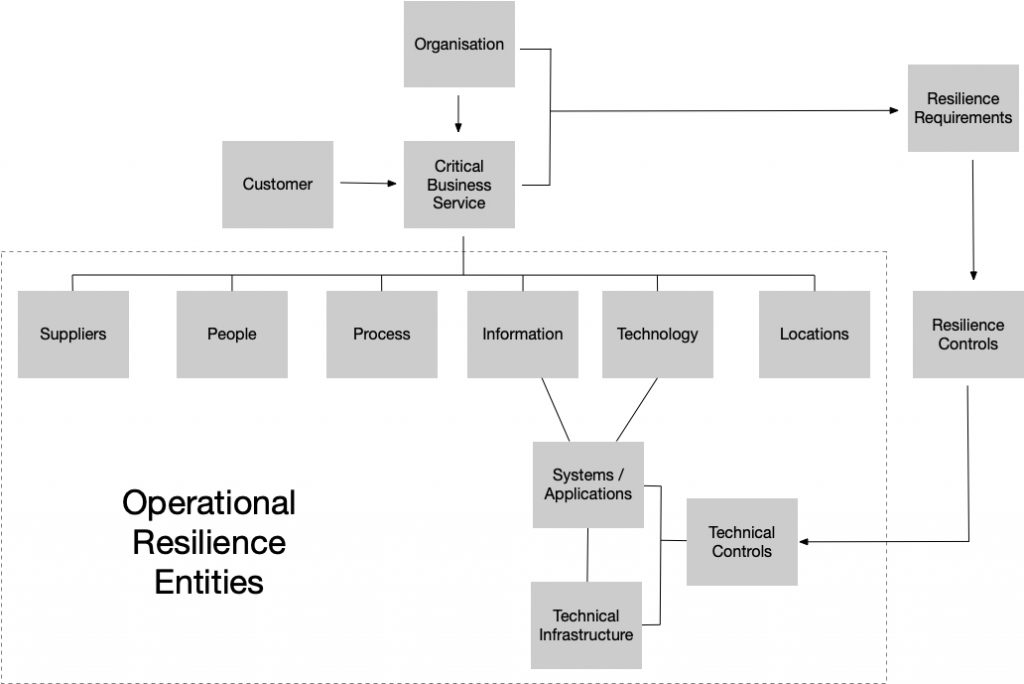
As you can see, when you focus on the information and the systems, infrastructure and technical controls, you only see a small slice of the necessary entities to deliver the critical business service. I admit I am doing a disservice to Information Assurance with that statement. The focus of the then doctrine risk assessment method IS1 was to start from information assets rather than customers and the services they consume, so it tends to describe the practice if not the theory.
Effective Cybersecurity needs us to consider the Customer and the Service they receive as the focal point with the much broader set of entities that contribute and are dependencies on successful delivery. Examples include:
- The loss of a supplier of plastic widgets to a destructive cyber attack on their manufacturing capability can be as damaging to the delivery of a service as a hacker getting into the critical systems and databases.
- The dependencies across multiple systems and information assets can highlight risks to service delivery that a focus on the individual information assets and the systems that hold them alone cannot see. For example data that is not a risk in a user facing system may be used in a more risky manner in a back-end reporting system that requires an end to end service view of the data flows and the data provenance and assurance.
- The automation of a manual business process can significantly reduce the cyber risk from a user being phished or conned, even better if the automation requires no user interaction.
A real challenge now with addressing cybersecurity risks to the service delivery is that many of the Resilience Controls we rely on exist outside of the Technical Control space that has traditionally been the IT Security / Cybersecurity comfort zone. We need to work closely with our business continuity and operational resilience colleagues. The embedding of core digital systems in the delivery of critical business services means that during a cyber-triggered disruption, the resilience and recovery of their service will often depend on alternative and sometimes manual delivery mechanisms.
Teams that come to rely on digital systems for their day to day work will reap the benefits of increased productivity, better-informed decisions and more accessible communications. However, they will also lose their ability to work without these systems unless we are proactive in understanding what a disconnected or disrupted digital environment looks like and prepare them to deal with it.
We should focus on protecting business services rather than protecting information assets.