I have had a series of productive discussions with a colleague over the last year about the differences in adopting new innovations between cyber attackers and cyber defenders. His interesting, and itself innovative, contention is that a key problem in cyber security is created by the differently shaped innovation adoption curves between defenders and attackers. Also that by investing in changing the shape of defenders adoption curves the nature of the competition itself will be re-shaped. (I suspect I am doing my colleague something of a disservice with my summary).
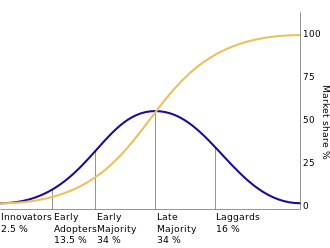
This comparison of innovation adoption rests on a strong body of academic economics research originally developed in the 1950s and effectively summarised by Everett M. Rogers in his book on the Diffusion of Innovations. I like the approach as it highlights the speed of action as a key component of cyber defence, in this case adopting innovative technologies or tactics, techniques and procedures (TTPs) quickly in order to respond to attackers innovations.
However, from my experience both advising CISOs and acting as an Interim CISO I do wonder if there is a related theory of innovation that applies. I would contend that most defensive security controls and TTPs are sustaining in nature as defined in Clayton Christensen’s controversial work in the Innovators Dilemma. Sustaining innovations show gradual improvement in contrast with disruptive innovations that jump to the next level of performance or value much faster.

The key problem of competition is that the most damaging attacks use disruptive innovations, potential black swans, that our sustaining defences cannot hope to defeat. My worry is that focusing on improving our speed of adoption of defensive innovations immediately places us at a disadvantage due to the sustaining nature of our defences. The serious and sometimes less serious adversaries jumped onto disruptive cyber attack innovations some years ago including industrialised attacks, camouflaged command and control channels, user-focused attacks and zero day or near zero day attacks.
I do think there is definite value here, I agree with Josh Corman that an unfortunate number of CISOs estimate their adversaries capabilities in relation to their auditors and external pen testers which places them squarely targeting defensive capabilities and adoption rates following HD Moore’s law leaving a serious gap between defensive and offensive capabilities from the most serious attackers. If we can highlight this issue CISOs and more importantly CEOs raise their game through improving speed of adoption of defensive cyber innovations, the next step is to ensure that the defensive innovations are effective against the disruptive offensive innovations.
My own contention is that measuring firms speed at traversing an Observe-Orientate-Decide-Act (OODA) loop (following Robert Boyd’s work on air fighter combat) is more effective as the the fundamental competition is one between the adversaries and the network defenders.

This shares concepts with a dogfight and once the fight has started the winner is the one that gets inside their opponents OODA loop first. If we can quickly adopt innovations that target the acceleration of our defensive OODA loops we stand a chance at not losing.
Automated IT infrastructure, automated incident response, cyber data analytics, pro-active threat hunting, information sharing, capability sharing and external hygiene monitoring of partners and suppliers are all defensive innovations that present us with the potential for ‘disruptive’ defences that may accelerate our network defence OODA loop. How’s your adoption rate on these technologies?
1 thought on “Competing Innovations in Cyber”
Comments are closed.