In my previous post, I introduced the Cynefin framework. The Cynefin framework provides a lens to understand the best approach to making decisions and taking action depending on the environment or landscape in which you are operating.
The Cynefin Framework immediately chimed with my experience of how we, as an industry, have approached information security, and latterly cybersecurity, over the years. Starting with compliance checklists, moving to a risk-based focus and then more to a capability maturity approach. We are now looking to cyber resilience as the new answer.
All of these approaches have had their failings over the years and have their champions and their doubters. My initial insight through considering the Cynefin Framework is that all of these approaches likely have merit simultaneously at the level of managing individual cyber events but that at the macro-level of approaching cybersecurity as a whole we are likely in the Complex domain and should make decisions using probe-sense-respond accordingly.
At the management or micro-level, the appropriate method depends on the nature of the cyber events we are trying to manage. Cyber events may or may not be incidents or breaches but all require us to make decisions and actions to achieve the optimal outcome.
NOTE: My diagrams here are deliberately the messy notes of my thinking. I wanted to reflect that this is something I am still considering and developing and didn’t want to give it the sheen of a finished concept.
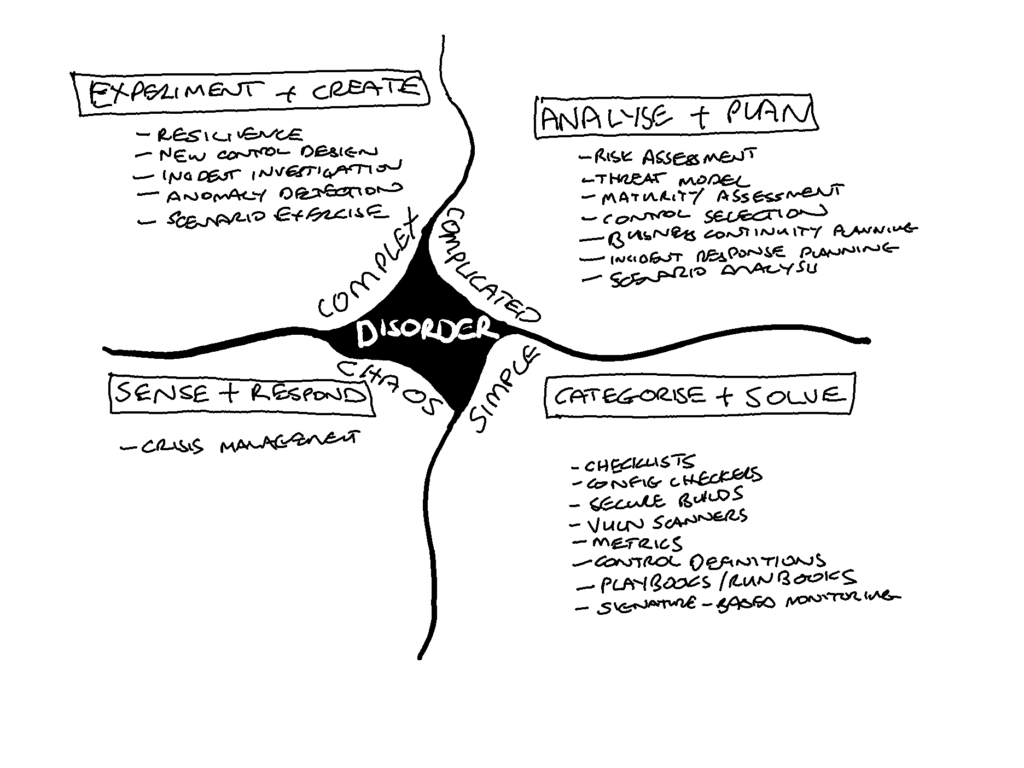
The failings we have seen may have been the result of misapplying compliance checklists in a complicated domain or of using risk assessment or capability maturity assessment in a complex domain. I wonder if one of the many problems we have improving our cyber hygiene is due to the application of risk-based methods to simple compliance issues, thus finding reasons not to do the right thing such as comprehensive and timely patching.
I think there is value in using this lens to understand which approaches or methods are appropriate to which cybersecurity events and ensuring that we use all of them.
That leads us to the need to understand the nature of the cybersecurity events. To understand how different cybersecurity events relate to the various domains of Cynefin, we must know something about the events explainability and predictability.
Cyber events are, mostly, as a result of human action and are more or less predictable. The event predictability reflects the goals and skills of the attacker as well as the range of possible events in the environment.
Attackers can be more adaptable to the environment as a result of their skill level and the degree of effort they are prepared to expend on a single instance of an attack.
The more adaptable an attacker is then the more extensive the variation of attack characteristics they would consider. With a broader range of attack characteristics to consider, we have greater uncertainty about the probable use of any specific set of characteristics. A more adaptable attacker has higher entropy in their attack space. Defending a higher entropy attack space requires either luck or greater resources as there are a wider set of defences and preparation required to increase our chances of success.
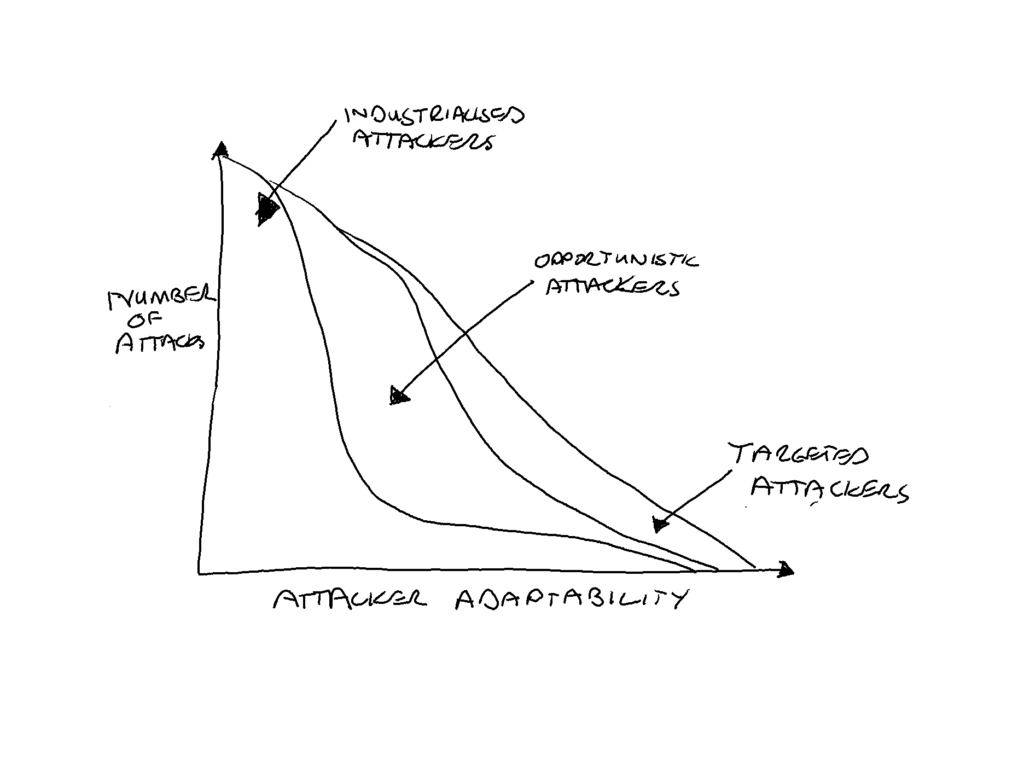
The motivation of an attacker to be more adaptable in any specific attack drives the acceptable cost of that attack to the attacker.
Attackers have bosses and budgets too.— Phil Venables (@philvenables) September 13, 2014
Low cost, low return but high volume attacks are by their nature more predictable. The Industrialised attacker’s attack space has a lower entropy level as the attacker focuses on the bottom line and is prepared to expend little effort to adapt to a single attack instance failing.
Medium cost, variable return attacks are harder to predict without knowledge of the extent of our exposure or our attack surface available to be exploited by these Opportunistic attackers.
High cost, high return attacks have a much higher entropy in their attack space making them difficult to predict without knowledge of these Targeted attackers, and the Targeted attacker must consider both the bottom line AND the top line but will be willing to expend more effort on adapting a single attack.
Defenders, however, can be more or less capable both as a result of preparation (processes, tools, etc.) and as a result of their technical skills. Operators require lower skill levels and rely on checklists, SIEM tools, automation and playbooks; Practitioners require greater analytical capabilities and rely on frameworks, network forensics and manual tooling; and Experts use reasoning and create custom tools and conduct threat hunting.
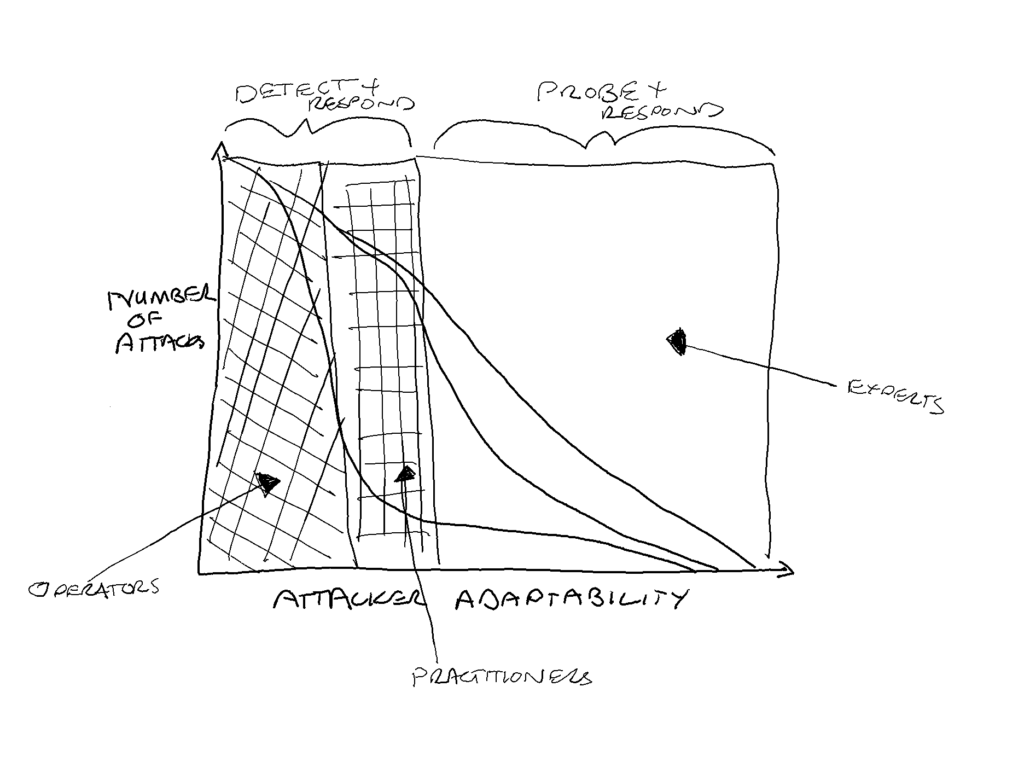
Investment of time and money in security ultimately drives the preparation and skills of the defenders.
Defenders can also invest in reducing the entropy in the attack space they must contend with. This reduces the uncertainty about the likely variation in attacks. There are two methods to do this, they can acquire more information on the attackers preferred methods through threat intelligence, or they can introduce controls to the environment that reduce or limit the available attack surface. Increasing the predictability of attacks can be done, but it will not eliminate the uncertainty.
Attackers, whose goal is to extract value online, and Defenders, whose goal is to protect value online, are not the only players in the cyber domain. There are the builders, whose goal is to generate and exchange value online and the consumers, whose goal is to consume and exchange value online. The behaviours of builders and consumers set much of the landscape of the cyber domain which is fought over by attackers and defenders.
It’s safe to say there are multiple agents (Attackers, Defenders, Builders and Consumers) interacting over a changing landscape (as new systems, features, attacks and defences are produced). There is variability between different agents, for example industrialised, opportunistic and targeted attackers, operators, practitioner and expert defenders and at a lower level between, for example, an organised criminal targeted attacker and a state targeted attacker.
I think these characteristics imply that cybersecurity as a whole is a complex adaptive system even if aspects of it are more predictable. This opens up an interesting possibility of the application of complexity theory approaches to the management of cybersecurity.
Considering the broader macro-level of cybersecurity through Dave Snowden’s Cynefin Framework opens up the possibility of applying complexity theory to the management of cybersecurity. Those concerned with the macro-level cybersecurity outcomes such as regulators, lawmakers and executives of the largest institutions should be prepared for more experimentation and use of probe-sense-respond rather than the codification of best practices and checklists. These likely still have a role at the micro-level for more predictable areas of the landscape such as cyber hygiene.
The encouragement of beneficial patterns and the discouragement of harmful patterns will need more attentive and responsive management of cybersecurity than many I suspect will want to hear. That said, the adoption of cyber resilience and the broader operational resilience lens is highly appropriate to the macro-level cybersecurity domain as it is grounded in a sense that the future events are unpredictable but that survival is predicated on an ability to adapt to and learn from the changing landscape and the events that take place.
This is the start of a process for me of trying to understand if there is a ‘physics of cyber’ as hinted at by this thread from ever-quotable Phil Venables:
Fundamental Drivers of Information Security Risk. A thread.
— Phil Venables (@philvenables) July 20, 2019
As I get older and (hopefully) wiser it has become ever more apparent that all the issues and risks we face arise from a small number of basic “forces”.
1/9
Please let me know your comments and thoughts.
NOTE: After I posted these blogs I was helpfully pointed to a much more eloquent exploration of Cynefin and Cybersecurity here. It confirms to me that there is definite applicability of the application of complexity theory to cyber decision making and that mashing out a couple of blog posts is not the same as a fully referenced and researched paper.
1 thought on “Making Sense of Cyber. Part Two.”
Comments are closed.