Cross-Domain Gateways are a concept from multi-level government and military networks that are increasingly being deployed into traditionally flat commercial networks. I’ve spoken before about ‘trust zones‘ and the concept of choke-points between trust zones concept combined with a view of the threat exposure for each trust zone underlies the need for cross-domain gateways. (Domain is the historical term commonly used in government and military settings for zones of trust.)
There are a wide variety of applications to which cross domain gateways can be applied and a wide variety of gateway patterns and designs. However there is a common set of possible gateway functions that such patterns and designs can commonly call upon.
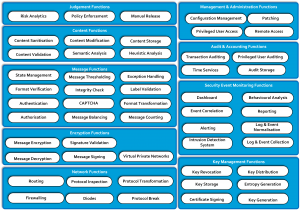
The following diagram indicates a reasonably exhaustive list of gateway functions that may be required depending on the threats faced, the assurance level desired and the application scope traversing the gateway.
Click on the image for a full size version.
The core cross-domain communication path functions are described in the Network Services, Encryption Services, Message Services and Content Services blocks. The supporting services that gateways often rely upon but may not be gateway specific include the Management & Administration, Audit & Accounting, Security Event Monitoring and Key Management blocks.
Not all functions are required nor desired in different gateways but all should be considered in their design, for example a gateway designed purely for automated machine to machine communications has different requirements and opportunities than one to pass interactive communications from a human.
There are no products on the market that can fulfill all of the functions and usually a gateway will require a mix of products with functional overlaps to ensure all necessary functions are delivered. The world is always messier than nice clean abstractions.
I’ve used this list of functions to successfully build a common language between multiple gateway designers who needed to cooperate on a large number of related gateways. It’s also useful when explaining to a well-informed reviewer of the subsequent patterns and designs which functions you decided not to include, it gives them a warm feeling to know that all such functions were considered even if for practicality or cost reasons they weren’t used.
Gateway Function Descriptions
Each of the functions has a short description below grouped by the conceptual function blocks they form part of. These aren’t intended to be complete merely enough to characterise the nature of each function.
Network Functions
Firewalling.
Firewalling is the process of applying a rule set to network traffic to ensure it meets the expected use of the network or system being protected.
Routing
Routing is the process of applying a rule set to network traffic to ensure it is transmitted to the permitted destination.
Protocol Break
Protocol break is the process of stripping and replacing the transport protocol headers from a network packet or stream to ensure that the transport protocol itself cannot be used to carry a covert channel. The replacement transport protocol headers may be the same protocol as was removed.
Protocol Inspection
Protocol inspection is the process of analysing the transport protocol headers to either compare against an expected range of options or to identify anomalous options or non-compliant headers.
Protocol Transformation
Protocol Transformation is the process of extracting the content of the application and/or transport protocols and reformatting it into a different application and/or transport protocol to ensure that any attacks on the transport or application protocol implementations are not transmitted from the gateway.
Diodes
Diodes are devices that only provide a unidirectional network connection.
Encryption Functions
Message Signing
Message signing is the process of cryptographically signing a message with a private key that can be verified using the certified public key of the sender to provide non-repudiation and authentication.
Signature Verification
Signature verification is the process of cryptographically verifying the signature of a message to provide non-repudiation and authentication.
Message Encryption
Message encryption is the process of rendering a message unreadable apart from to a recipient who can use a valid cryptographic key.
Message Decryption
Message decryption is the process of rendering an encrypted message readable using a valid cryptographic key.
Virtual Private Networks
The provision of point to point encrypted network tunnels to provide authentication of end points and confidentiality of data in transit.
Message Functions
Authentication
The process of determining the originator of a message is the identity they claim.
Authorisation
The process of verifying the originator of the message has permission to access the data or execute the action they are requesting.
Integrity Check
Integrity Checking is the process of verifying that a message is unchanged, when it has been received from the originator or when the message transits the gateway or when the message is transmitted to the recipient.
CAPTCHA
CAPTCHA is an acronym for ‘Completely Automated Public Turing test to tell Computers and Humans Apart’. This is a challenge/response test that requires the user to complete a task that is difficult for a computer to complete but easy for a human to complete. The goal is to ensure the user is a human being and not a bot of some form.
Message Counting
Message Counting is the process of ensuring that the number of messages relating to a complete transaction matches the expected number of message for that transaction type. For example this could describe the process of ensuring the number of responses to an endpoint matches the number of requests from that endpoint.
Message Balancing
Message Balancing is the process of ensuring that the appropriate responses are transmitted compared to the requests. For example this could describe the process of ensuring that Request Type A is only ever answered with Response Type A and not Response Type B.
Format Transformation
Format transformation is the process of rewriting the content of a message into a new messaging format while maintaining semantic consistency. For example this could include rewriting an XML message from one schema to another.
Label Validation
Label validation is the inspection and verification that content meta-data within the message meets predetermined criteria.
Message Thresholding
Message Thresholding is the process of ensuring that multiple messages received or sent over a period of time meets the normal expectations of the business process activity.
Format Verification
Format verification is the process of verifying that a message is correctly formatted in the expected format.
Exception Handling
Exception handling is the process of safely handling messages that fail one or more steps of the message validation process.
State Management
State management is the process of maintaining session states with systems on either side of the gateway that are unaware of each other. Some protocols are stateful and as such the gateway must ‘break’ the session state internally for the purposes of the security enforcing functions within the gateway but maintain a session externally.
Content Functions
Content Sanitisation
Content sanitisation is the process of removing any detected malicious content while retaining the non-malicious content of a message for transmission.
Note: This is notoriously hard and is not recommended where higher levels of assurance are required.
Content Validation
Content validation is the process of checking that the content of a message is correct and makes sense. For example a message may contain an employee’s name and that may be checked against an internal directory to check that person is an employee.
Content Modification
Content Modification is the process of altering the content of a message as it transits a gateway following pre-determined rules for the alteration. This could include replacing an employee’s name in a data record with their staff number.
Content Storage
Content Storage is the process of storing and retaining content within the gateway. This is commonly used to retain the originally received versions of content including any integrity checks from outside the gateway before transforming a message or modifying the content to ensure the original content remains available.
Semantic Analysis
Semantic Analysis is the process of attempting to ‘understand’ the meaning of a message. This may allow for the detection of coded speech.
Note: While this is a rapidly developing field of computer science as yet there is little assurance available in the effectiveness of these techniques.
Heuristic Analysis
Heuristic Analysis is the process of applying a statistical comparison between known bad content and unknown content to identify previously unknown bad content. This is common approach used by Anti-Virus software that attempts to analyse software behaviour and/or source code for its similarity to malicious software.
Note: This is generally ineffective against custom attacks because there is nothing to compare against.
Judgement Functions
Risk Analytics
Risk analytics is the process of risk scoring a particular message or communication by examining a variety of message or content characteristics combined with historical judgement of those characteristics.
As an example a higher risk internal user may be able to communicate over the gateway until those communications reach a certain threshold of content per day or hour or until the gateway identifies other riskier communications occurring at the same time. There can be a wide range of different message, content and historical characteristics to be considered in setting the risk judgement criteria.
Manual Release
Manual release is the process of ensuring an appropriately trained and informed administrator must take a final decision on releasing content from the high to low domain.
Policy Enforcement
Policy enforcement is the process of applying pre-determined business rules as a result of analysing the content of a message.
Key Management Functions
Entropy Generation
Entropy generation is the generation of random data to form the seed for key generation.
Key Generation
Key generation is the creation of keys for encryption and signing.
Key Revocation
Key revocation is the process of marking an existing key as invalid and communicating that marking to relying parties.
Key Storage
Key storage is the storage of encryption and/or signing keys to prevent unauthorised use, disclosure or tampering of those keys.
Certificate Signing
Certificate signing is the process or cryptographically signing a digital certificate that contains both a public key and the identity of the key owner.
Security & Event Monitoring Functions
Log & Event Collection
Log and Event collection is the process of collecting all the component level logs and alerts into a central point.
A key characteristic of log and event collection is to ensure the integrity of the logs or events from the point of generation back to the point of analysis as these are likely to be a high priority target for attackers wishing to cover up their activities in order to maintain a foothold in the system over a period of time.
Log & Event Normalisation
Log and event normalisation is the process of transforming the logs and alerts from the different components of the gateway into common language and structure to facilitate analysis.
Intrusion Detection System
An Intrusion Detection System is a host or network based tool for monitoring activities or communications for malicious intent and producing alerts when discovered.
Alerting
Alerting is the process of individual components, Intrusion detection Systems or event correlation components notifying another system or a human operator that a suspicious or malicious event has occurred.
Alerting usually has a goal of notifying another system or a human operator in as short oa period of time as possible following the identification of the event.
Reporting
Reporting is the process of providing retrospective analysis of security relevant events over time to facilitate trend analysis and management planning.
Reporting is usually conducted regularly over period of time such as daily, weekly or monthly.
Event Correlation
Event correlation is the process of analysing logs and events that in individually do not represent a high probability of malicious activity but that in combination provide clear indicators of an attack. Such composite events can rely on lower level log records and events from many components.
Dashboard
A dashboard is a summary screen of the health and status of a security gateway. It can include system maintenance relevant metrics and commonly includes Reporting output and a view of Alerts or Correlated Events from the recent past.
Behavioural Analysis
Behavioural analysis is the process of analysing logs and events for unusual patterns of system or user behaviour against the baseline of normal behaviour seen in the gateway. Similarly this can be to look for patterns of system or user behaviour that are indicative of malicious activity.
Audit & Accounting Functions
Audit Storage
The storage of transaction logs to prevent unauthorised access, disclosure, tampering or the loss of the logs.
Transaction Auditing
Transaction auditing is the process of recording the security relevant characteristics of business transactions as they occur.
Privileged User Auditing
Privileged user auditing is the increased auditing specifically enabled to track the activities of users on a gateway such as administrators or engineers when they assume higher privileges such as the ability to change the configuration or delete log files.
Time Services
Time services provide the reliable synchronisation of the clocks of all components across the gateway.
Management & Administration Functions
Configuration Management
Configuration management is the process by which necessary change is managed and assured. This is a critical activity to maintain the security of a gateway through it’s deployed lifetime.
Integration of the gateway administration function into the high and low domains change control processes is a challenge.
Privileged Access Management
Privileged access management is the process and technologies to control and restrict user privileges such as read of data passing the gateway, changes to the configuration of the gateway or deletion or modification of security logs.
Where such elevated privileges are not required for day to day activity they should be placed under a ‘break glass’ process which may require a technical tool to implement.
Patching
Patching is the process by which functional flaws and security vulnerabilities are addressed through the lifespan of the gateway. It is critical to understand how patches are validated before being applied to the gateway and how they will be imported to the gateway system as this route provides an opportunity for attack.
Remote Access
Remote access is the ability to manage a gateway without standing at the physical consoles of the components that make it up. This presents an attractive target to an attacker hoping to bypass or subvert a gateway and must be protected to a high degree.
Note: In very high threat environments it may be that sufficiently high assurance remote access is not possible and as such console administration is necessary.