Back in 2015, I presented a few times on some insider risk management work I had been doing. A recent conversation with a colleague suggested I should make some of those presentation materials more easily consumable as a blog post.
Insiders are legitimate, trusted, individuals we rely on as part of our business activities. These trusted individuals use our assets in a manner that could cause harm to the organization or other people we have a duty of care to protect. Insiders may not mean to cause harm, they may be negligent, they may have been tricked or coerced. Insiders may not cause immediate harm but their actions may increase the likelihood of harm.
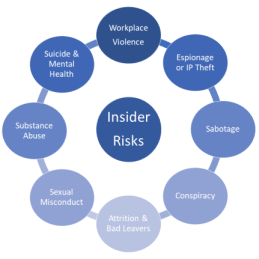
More and more Insider incidents are in some way cyber-related, it is increasingly less useful to single our ‘cyber-insiders’ as a separate risk.
89% of Insiders have no criminal history, having never been charged or convicted of a crime. Extensive research has shown that there is no ‘profile’ of an insider, no set of measurable characteristics by which they can be reliably identified from a general population.

There are risk factors to any member of staff becoming an insider, these change over time due to actions by the member of staff, due to their changing circumstances and as a result of actions by the company. The opportunities for an organisation to manage this risk are spread across a wide range of functions including; human resources, legal, corporate investigations, IT security, audit, executive leadership and others.
It is unlikely a coherent insider risk management programme will emerge without a holistic view of the risk and the factors associated with it.
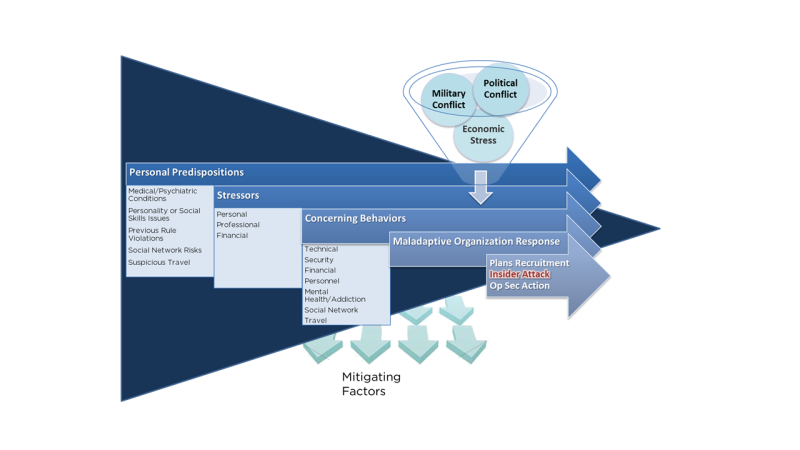
The Critical Pathway to Insider Risk, a concept developed by Eric Shaw with a number of colleagues in the CIA and the FBI, is one of the key tools to understand the journey a trusted insider takes in order to become a malicious insider.

Many valued trusted insiders will move along the critical pathway and yet will not become a problem. However, the key to an organizations response is to identify trusted insiders with high-risk factors and intervene to manage that risk.
Personal predisposition provides the foundation, personal stressors and environmental stress or conflict exacerbate negative traits which lead to an insider exhibiting concerning behaviours. An organizations response to these concerning behaviours, ranging from ignoring them to inconsistency or overreaction can then push an insider into action.
It is possible to invest in mitigating factors that reduce the opportunity and the impact of harmful insider activities, these need to be combined with monitoring for risk factors to pro-actively identify and intervene in insider risks.
Mitigating factors for Insider risk across the entire insider lifecycle include a range of controls and mitigations from technical controls through processes and exhibited leadership behaviours and culture.
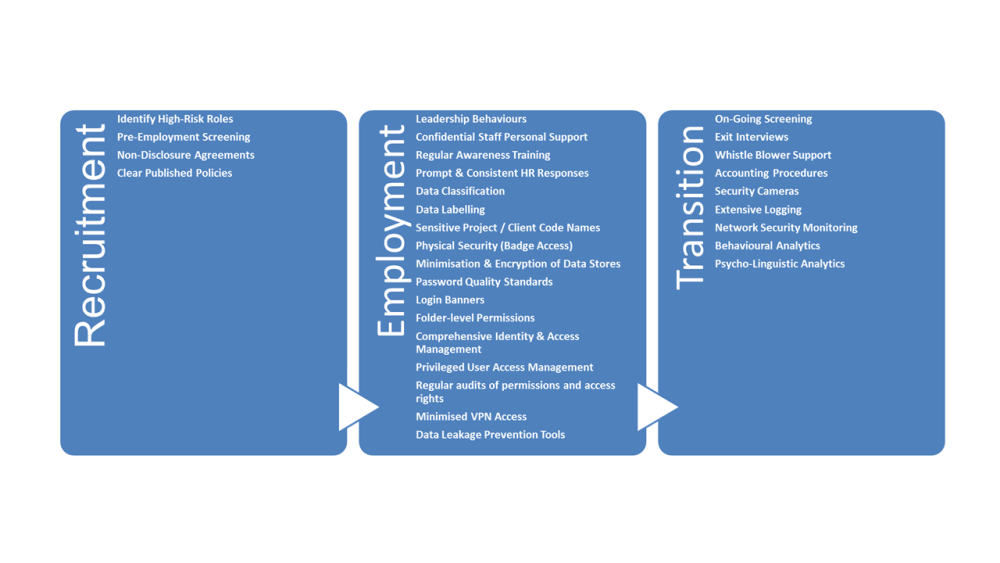
No one role or team can own and implement all of these, these are cross-enterprise controls that need to be implemented, managed and monitored as an enterprise risk. Frankly, the scope of the risk is such that if it is led from the security team it is much less likely to succeed. The security team are a key contributor but should not own this risk.
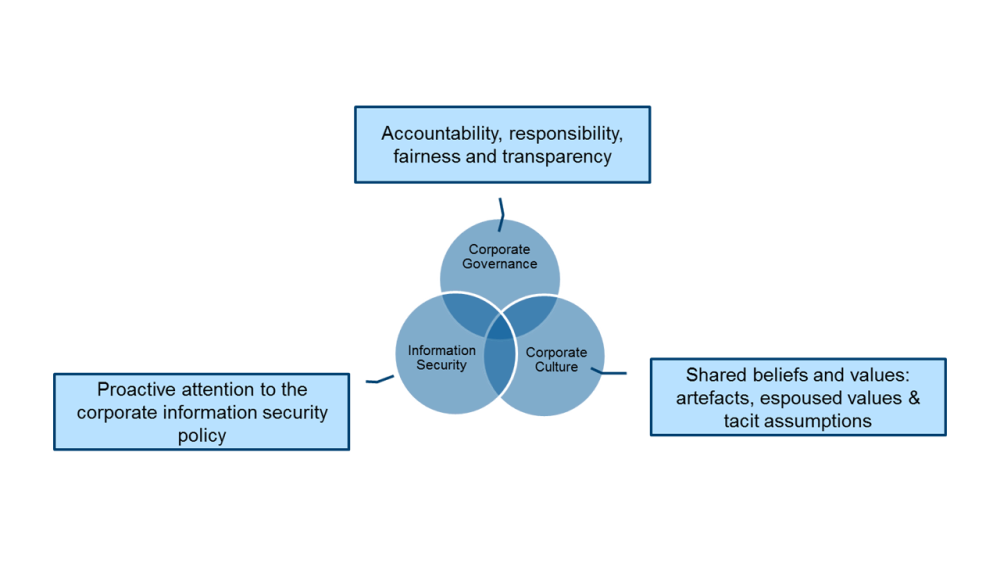
Many teams need to have responsibility and accountability for different aspects of the insider lifecycle and Key Performance Indicators need to reflect the needs of the management of the Enterprise-wide risk.
The coverage, effectiveness and maturity of controls and processes should be measured and included in annual audit activities to ensure they remain part of ‘business as usual’ activities.
I hope this is useful as a frame and a starting point for examining insider risk in your own organisation.