During my career, I have helped several firms design and operate supply chain cyber risk management (SCCRM) programmes. I have some ongoing concerns that I have posted about before about the industry focus on self-reported checklists of various quality. I also have some heightened concerns regarding the use of externally…
Category: Security
Security on the Bottom Line
I often hear calls for security to be treated as a business issue. This seems to vary from calls for the Board of Directors to take an increased interest in security to calls for CISOs to raise their gaze from the technology and consider the whole business. I have myself…
Serious Business?
Regulating cybersecurity, and data protection in general, is driven by two needs; to clearly explain the expectations that society has for the organisations that society is increasingly dependent on, to provide a mechanism for the unmanaged externalities to those organisations (the societal and personal harm from breaches) to be realised…
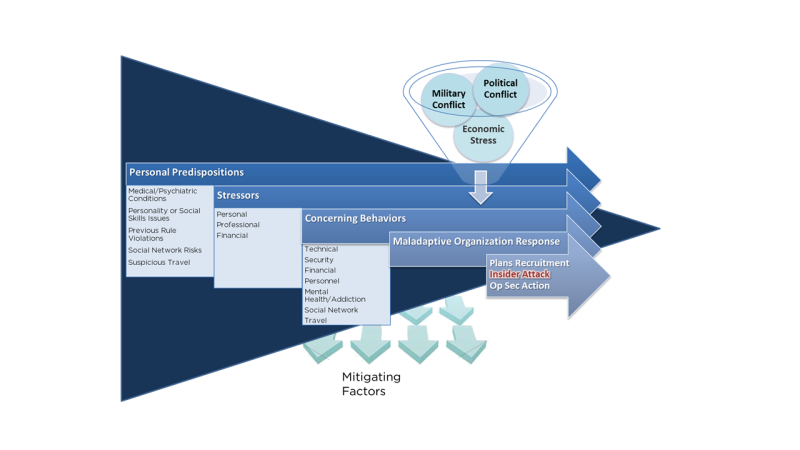
Insider Risk Management
Insiders are legitimate, trusted, individuals we rely on as part of our business activities.
Making Sense of Cyber. Part Two.
In my previous post, I introduced the Cynefin framework. The Cynefin framework provides a lens to understand the best approach to making decisions and taking action depending on the environment or landscape in which you are operating. The Cynefin Framework immediately chimed with my experience of how we, as an…