The role of security in business is constantly up for debate, a growing movement in the UK around adopting some of Simon Wardley‘s approaches to strategy to a security strategy has started some interesting conversations again. For years security was seen as the department of no or the guys that…
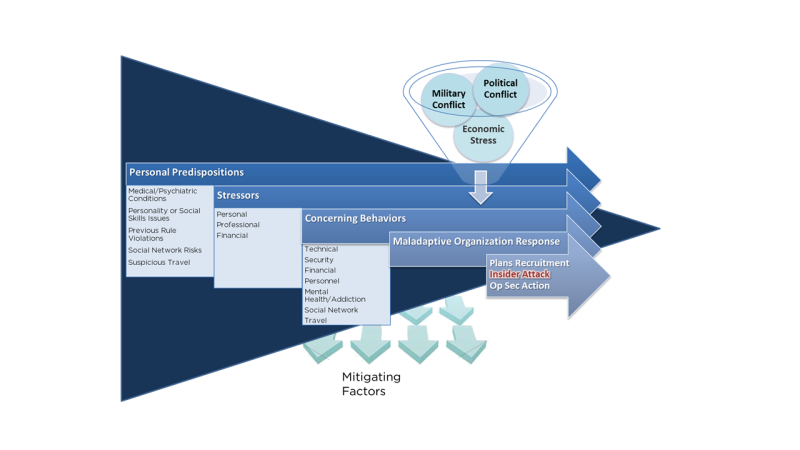
Insider Risk Management
Insiders are legitimate, trusted, individuals we rely on as part of our business activities.
Making Sense of Cyber. Part Two.
In my previous post, I introduced the Cynefin framework. The Cynefin framework provides a lens to understand the best approach to making decisions and taking action depending on the environment or landscape in which you are operating. The Cynefin Framework immediately chimed with my experience of how we, as an…
Making Sense of Cyber. Part One.
I recently attended the Open Security Summit. While there, I met Dave Snowden, who introduced me to his Cynefin Framework, which has sparked a bit of a journey for me ever since. Cynefin is an interesting welsh word with no real English translation but has been described by “It describes…
Information Security Risk Universe
In my previous post, I introduced the concept of a ‘Risk Universe’ which I flesh out in more detail here. A Risk Universe provides a comprehensive view of the possible risks we face to aid in categorisation but also to act as a check on the scope of our risk…